
My journey into the world of internet fakes
Frederick Scholl October 07, 2020

Frederick Scholl October 07, 2020

What happens when the information we see cannot be relied upon? During our present time of social isolation, we are even more dependent on what we see on the screens before us. Data integrity is the second leg of the security CIA triad of confidentiality, integrity and availability.
My recent experience on Amazon brought home some of these issues. I often browse for new cybersecurity books. A 2020 book, Cybersecurity by Elijah Lewis, caught my eye. It promised to be “A comprehensive beginner’s guide to learn the realms of cybersecurity from A-Z”. It also had 4.5 stars and glowing reviews. I plunked down $17.99, hoping to find some good material for teaching cybersecurity.
Amazon’s prompt delivery came through. After opening the book, I was surprised to find no author biography. I also started having trouble finding any real content in the 107 pages. No diagrams? Then I parsed some of the language in each chapter:
You get the picture. I started to wonder if the book was written by an AI (Artificial Intelligence) program. I went to the “Author Page” on Amazon. Nothing there, although Mr. Lewis has written several additional books. Then I went to LinkedIn to find a profile for him. Nothing there, either.
Next, I went back to the Amazon reviews. Who were the reviewers? John S. reviews books on cybersecurity, hydroponics and pregnancy; Julie reviews books on cybersecurity, cricket and vegetarian cooking! I didn’t see any reviewer with real qualifications. Are they fake also?
Finally, I enlisted some technology advice. Fakespot is a site that evaluates online reviews (www.fakespot.com): a reviewer’s reviewer. It looks at the reliability of those reviews. Below is the result after checking my book’s reviews: an F — not good in academia.
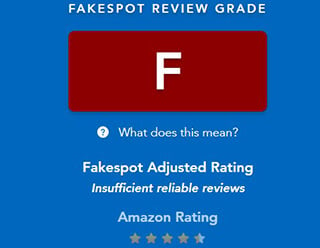
I do thank Amazon for readily granting me a refund on this book. They were also very polite in posting my one-star review “This book is a fake” (“We and millions of shoppers on Amazon appreciate the time you took to share your experience with this item”).
What I learned is that we can all be easily scammed. I’m always looking for good books on cybersecurity and I hit “Buy Now” faster than I should have. According to the Washington Post, certain product categories like weight-loss and Bluetooth headphones already have 50-70% questionable reviews. Now we can add cybersecurity to books to that list.
Broaden your skills with Quinnipiac's MS in Cybersecurity online program. Learn how to mitigate business risks through information security process improvements from industry thought leaders.
Quinnipiac Today is your source for what's happening throughout #BobcatNation. Sign up for our weekly email newsletter to be among the first to know about news, events and members of our Bobcat family who are making a positive difference in our world.
Sign Up Now