
Protecting you and your small business against ransomware
Frederick Scholl March 01, 2020

Frederick Scholl March 01, 2020

This blog post looks at the threat and makes specific recommendations you can use to reduce the chance you will be a ransomware victim. Of course, there are no silver bullets to protect you, but if you are more secure than the next potential victim, you will be a lot safer.
These attackers go after targets of opportunity that can be breached with the least amount of effort.
Being aware of the ransomware threat is your first line of defense. What exactly is the threat?
It is a criminal business. The ransomware business is a well-organized criminal enterprise with you as the target.
Forget the idea of one lone hacker in his basement. The adversary is much more sophisticated. The global supply chain we are up against includes ransomware developers, exploit kit developers, affiliates, distributors and you, the target organization.
Three trends have led to the resurgence of ransomware: the rise of cryptocurrencies like bitcoin; the rise of free malware, circulating on the dark web and the economic challenges felt by most people around the globe. Only 10% of the population has more than $65,000 in assets.
That leaves over 6 billion people with fewer assets.
The next question is how do attackers penetrate your network? Recent statistics show that over half of attacks come through a remote access weakness. (Thanks to Bill Siegel, CEO of Coveware for some of these statistics.)
RDP vulnerabilities have been at the top of the list. Next are the well-known phishing attacks. Third are software vulnerabilities, most commonly related to unpatched systems.
Next, who are the preferred targets? The top four sectors are: professional services, healthcare, software services and public sector.
So how to protect yourself, beyond just being aware of these statistics? First of all, configure your antivirus solution to block ransomware processes. Second, maintain an air-gapped backup.
The first “prevent” defense is to stop the attack from occurring. The second enables you to recover if attacked.
Traditional anti-virus searches your machine for malware and bases alerts on signatures distributed out to user workstations or servers. Ransomware detection operates differently and monitors access to your protected files by unknown programs running on your machine.
Windows 10 already includes this feature; you just need to make sure it is configured properly. Go to Settings/Windows Security/Virus and Threat Protection/Ransomware Protection/Controlled Folder Access.
You should make sure that protection is “On” and that you have all your important files protected.
Some people may prefer to use third-party vendors for this protection. Malwarebytes is one I have used. It also has other valuable features such as identifying fraudulent web sites that you may be trying to access.
Once you have protection in place, you need to implement means for recovery. No protection software will be 100% effective. This means backups of your important data.
Most people will already be doing this, but to protect against ransomware, you need to have at least one copy of your data offline. This means not accessible without physically installing the backup copy on your PC or server.
Smart ransomware will look for attached data and go ahead and encrypt that. In that case your primary and backup data will both be encrypted. I have recently started using Veeam backup software, Community Edition.
Veeam is an enterprise grade backup solution, however, the Community Edition is free and will backup up to 10 workloads. I have been using it and think it is great. I backup at night when I am not using my computer and then remove the backup drive during the day.
So, I have at least one air-gapped drive available.
The screen shot below shows a snapshot of recent backups.
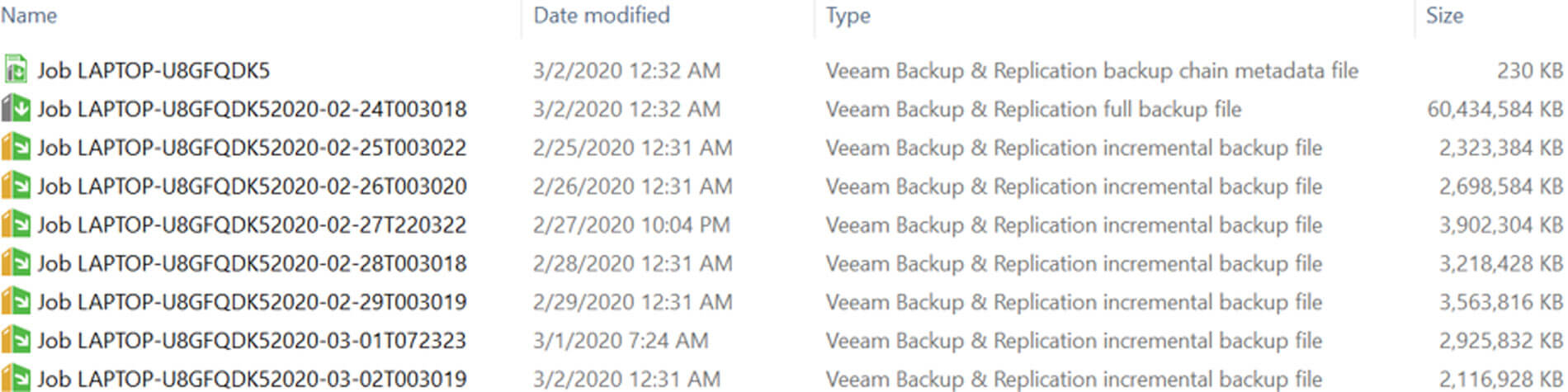
Veeam first takes a full backup. Then every day it takes in incremental backup of files that have been changed. The key to all this is the metadata file that allows you to easily restore each file. For me, this represents peace of mind in a risky world.
If you are looking to bring your company's security to the next level, Quinnipiac’s MS in Cybersecurity focuses on training technically proficient security defenders to do just that.
Our program is a broad, hands on 30 credit hour curriculum planned and taught by top business and security professionals.
Quinnipiac Today is your source for what's happening throughout #BobcatNation. Sign up for our weekly email newsletter to be among the first to know about news, events and members of our Bobcat family who are making a positive difference in our world.
Sign Up Now